Securing a network for IoT

Alexa, Google Home, Siri – the new revolution of computing power is the spoken word. You just tell a device what you want and – voila – it happens. But in order for stuff to happen – say turning lights on – a few of things have to be considered to create a safe environment.
So you have an Alexa device configured and working (we use “Alexa” as a general term for all voice assistants) Great. You can listen to music, set timers, get the news which is very cool. Now – you want Alexa to control a light switch or a power outlet? Let’s get started.
But you need to know a few things first:
 Every IoT (“smart”) device needs to be able to receive digital commands. But your network is (I hope) securely sitting behind a router or WiFi access point. Those units use a technology called “NAT” to talk to the outside world. This is good and bad. It’s good that “NAT” protects your computers and other networked devices from unwanted connection requests. It’s bad because that also prohibits any “call” to your wireless outlet. And if Alexa can’t connect to your outlet, it won’t be able to turn it on or off.
Every IoT (“smart”) device needs to be able to receive digital commands. But your network is (I hope) securely sitting behind a router or WiFi access point. Those units use a technology called “NAT” to talk to the outside world. This is good and bad. It’s good that “NAT” protects your computers and other networked devices from unwanted connection requests. It’s bad because that also prohibits any “call” to your wireless outlet. And if Alexa can’t connect to your outlet, it won’t be able to turn it on or off.
In order to circumvent the NAT mechanism, the manufacturers of “smart” outlets or devices have own servers deployed. It works like this: Your power outlet connects to the manufacturers server (outgoing connections are always passing through “NAT”) and keeps the channel open. The manufacturer service is reachable by Amazon’s Alexa se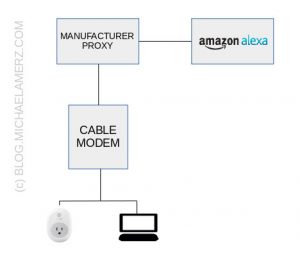 rvers. So if you tell Alexa to turn the light on, Alexa doesn’t directly connect to your power outlet, it connects to the manufacturers proxy server which uses the open connection to your device to tell it to do something.
rvers. So if you tell Alexa to turn the light on, Alexa doesn’t directly connect to your power outlet, it connects to the manufacturers proxy server which uses the open connection to your device to tell it to do something.
We now have two security concerns: First: If someone hacks the manufacturers server, they can turn your stuff off and on. The only way we can deal with this is to not use IoT with critical systems. While it may be fun to voice control grandpa’s oxygen concentrator – it is not recommended. The second security concern is the device itself. Every “smart” device, switch, power outlet, light bulb or thermostat is basically a small computer – hooked up to your (wireless) network. Most are produced in China and you (I, we .. ) have absolutely no idea, what’s going on in there. It could spy on you, steal from you, it could be used to access your phones or computers, even plant malware or viruses. You need to protect yourself.
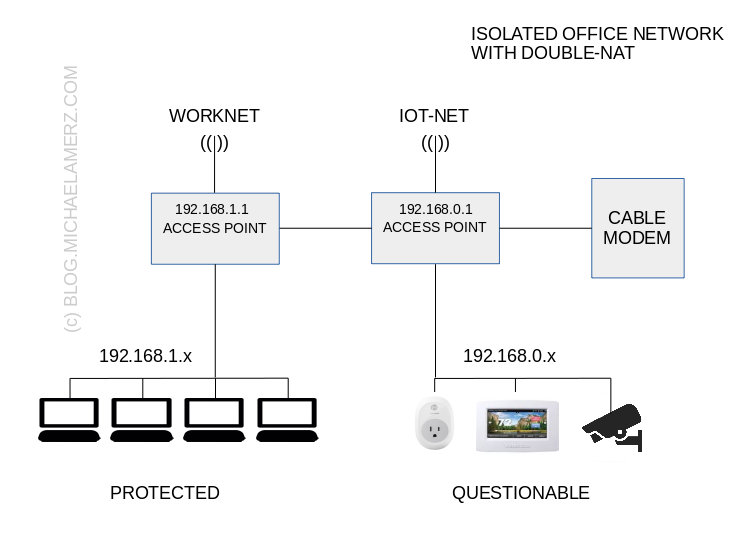 Double-NAT is the answer. Remember when I told you about NAT blocking unwanted connections? This is what we do here too. We simply connect another access point to the one we have. What will this accomplish? While you will be able to work as usual within your network, the “smart” devices will not be able to access any computer or device behind the second NAT. Even if any of those “smart” devices is or becomes malicious, your devices behind the second access point are out of reach. Since NAT works like a valve allowing data downstream but not upstream, any device after the second access point (192.168.1.1) can connect to any device within the full network, but devices behind the first access point (192.168.0.1) can only see other devices in this section.
Double-NAT is the answer. Remember when I told you about NAT blocking unwanted connections? This is what we do here too. We simply connect another access point to the one we have. What will this accomplish? While you will be able to work as usual within your network, the “smart” devices will not be able to access any computer or device behind the second NAT. Even if any of those “smart” devices is or becomes malicious, your devices behind the second access point are out of reach. Since NAT works like a valve allowing data downstream but not upstream, any device after the second access point (192.168.1.1) can connect to any device within the full network, but devices behind the first access point (192.168.0.1) can only see other devices in this section.
Enjoy your safe(r) network. And follow me on TWITTER.